Understanding Suspicious Requests on Your Server
If you’ve ever checked your server logs and found strange, unsolicited requests hitting your API, you’re not alone. Many developers notice these unexpected access attempts and worry that their application might be under attack. However, after investigating this phenomenon, I discovered that not all of these requests are malicious. In this blog post, I’ll share my findings and how you can analyze similar requests on your server.
My Investigation into Suspicious API Requests
Like many developers, I frequently noticed unknown IPs making requests to my APIs. These requests often contained unusual payloads or attempted to access endpoints that didn’t exist in my application. To understand what was happening, I decided to investigate.
Step 1: Extracting IP Addresses from Logs
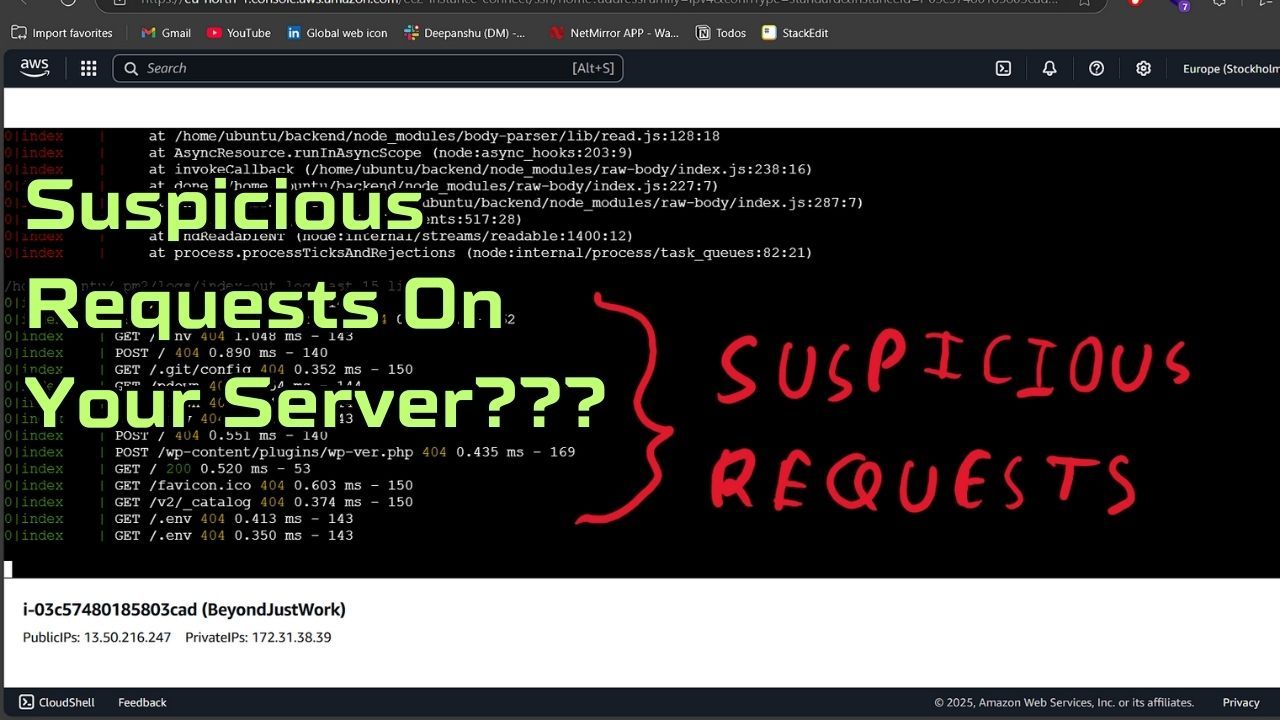
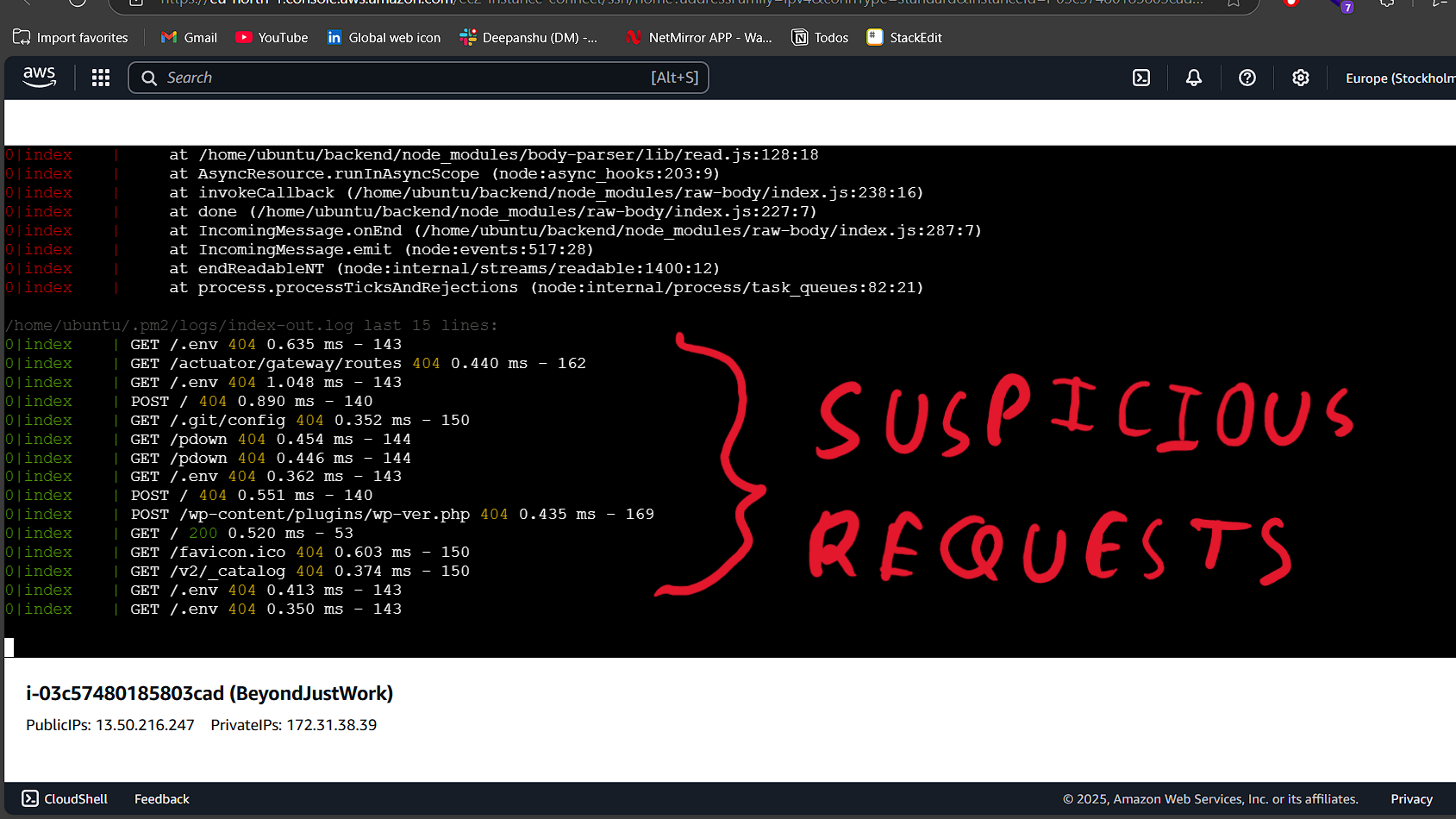
The first step in my investigation was to check my Nginx logs to extract the IP addresses making these requests. If you’re using Nginx, you can find the logs in the following location:
/var/log/nginx/access.log
To filter requests from a specific IP, I used the following command:
grep "suspicious_endpoint" /var/log/nginx/access.log
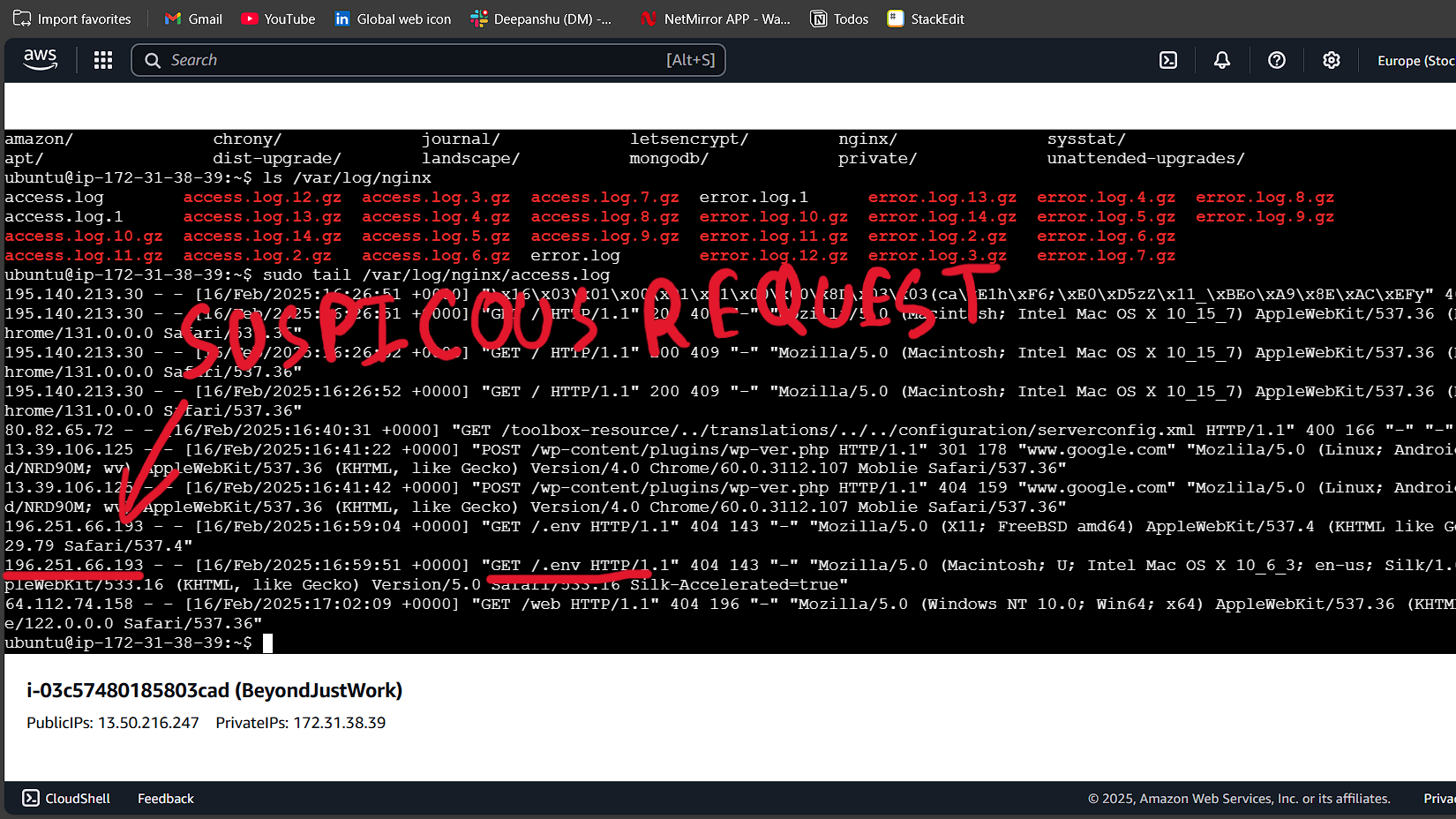
This command helped me identify multiple unknown IPs that were probing my API.
Step 2: Tracing the IP Addresses
Once I had a list of suspicious IPs, I used an online IP lookup tool (such as ipinfo.io or Whois Lookup) to gather information about these addresses.
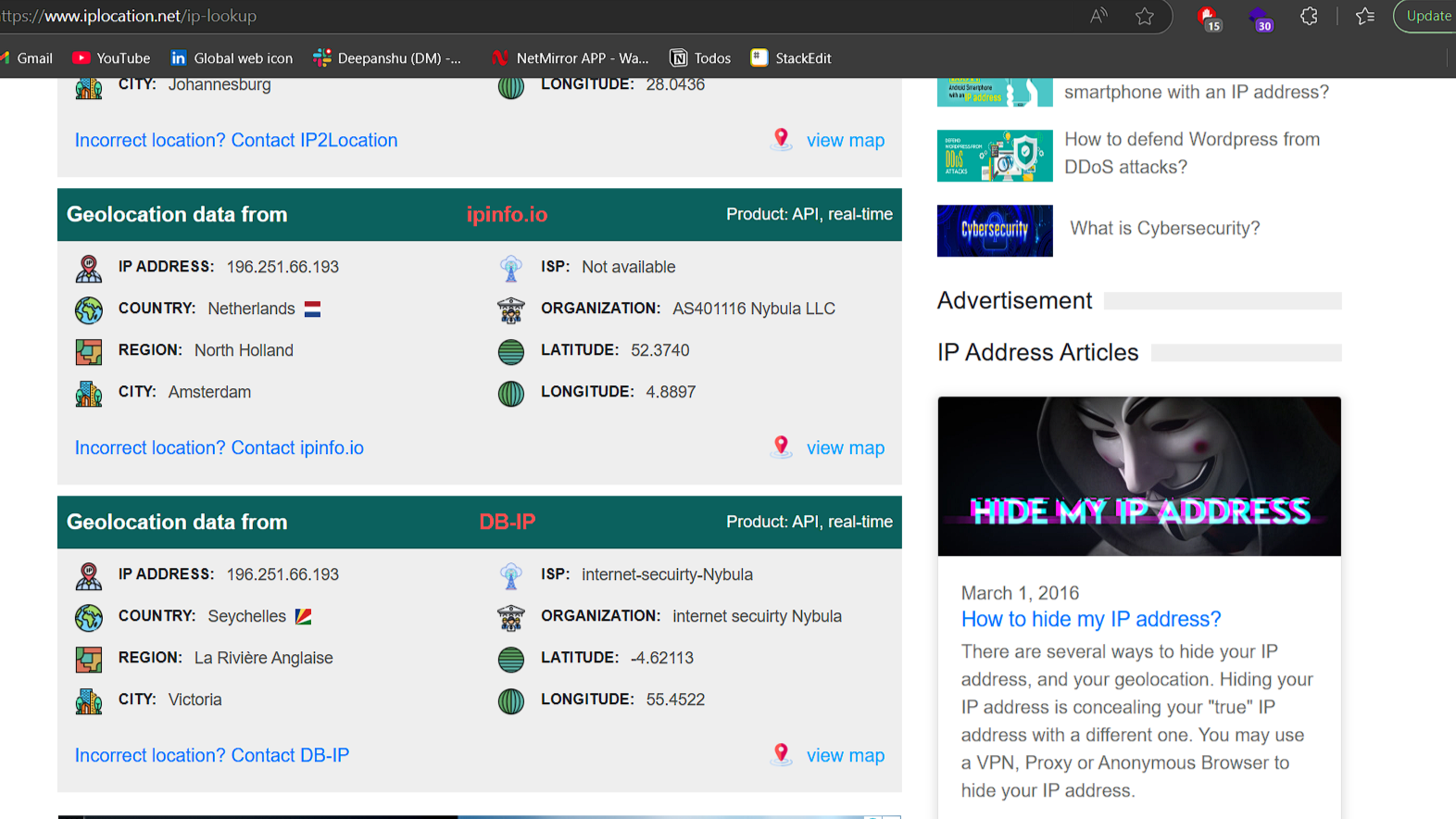
Surprisingly, many of the IPs I traced were linked to cybersecurity companies. The ones I was able to track down belonged to firms that specialize in penetration testing, vulnerability scanning, and security services.
Why Are Cybersecurity Companies Probing Your API?
After further research, I found that these companies run automated scripts to scan publicly accessible APIs and websites for vulnerabilities. Their goal is to identify security weaknesses, such as misconfigured authentication, open endpoints, or exploitable API keys. If they find an issue, they may contact you to offer their services or report the vulnerability.
Are These Requests Harmful?
While these automated scans aren’t directly malicious, they can expose security flaws if your API is not properly protected. Attackers also use similar techniques, so it’s important to take these requests seriously and implement strong security measures.
How to Protect Your API
If you’re seeing these types of requests in your logs, consider the following best practices to secure your API:
Use Authentication & Authorization
Implement authentication (JWT, OAuth, API keys) to restrict access.
Use role-based access control (RBAC) to limit permissions.
Rate Limiting & Throttling
Prevent excessive requests from the same IP address.
Services like Cloudflare, Nginx, or API Gateway can help.
Monitor & Log Requests
Regularly check your server logs for unusual activity.
Set up alerts for potential threats.
Use Web Application Firewalls (WAFs)
Deploy a WAF to filter out malicious requests before they reach your API.
Keep Dependencies Updated
Ensure your API framework, libraries, and dependencies are up-to-date.
Conclusion
Seeing suspicious requests on your API can be concerning, but not all of them indicate an attack. Cybersecurity firms often scan public APIs to identify vulnerabilities. However, bad actors use similar techniques, so you should always be prepared with proper security measures. By monitoring logs, securing your endpoints, and implementing best practices, you can protect your application from unwanted access.
Share Your Experience
Have you encountered strange requests in your server logs? How did you handle them? Let me know in the comments!
Add screenshots showing:
A suspicious request in Nginx logs.
An IP lookup result showing a cybersecurity company.
Example of a WAF blocking an unusual request.